The Cyber Trust Mark is a new smart device label created by the US government to prove that a...
Larilyn’s Tip of the Week: Consent Phishing
When it comes to technology, there are two things that are certain:
- Because there are so many bad guys out there trying to gain access to your information, security measures are constantly improving and changing.
- The bad guys aren’t just bad – they are also smart. And with every changing security measure, they start figuring out how to work around it.

A few years ago, multi-factor authentication became a huge step forward in log-in security. When you log into an account, like your Gmail for example, you don’t just need your password. You also get sent a text message with a code to input.
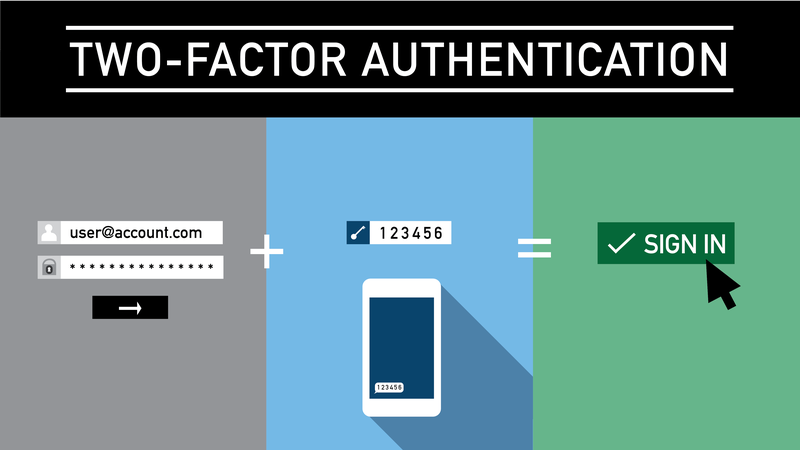
This made things safer because even if someone could figure out your password, they still couldn’t get into your account unless they had that code you were sent.
And for awhile, everything was unicorns and rainbows.

But then those pesky smart bad guys. They figured out a workaround. You knew it was coming, didn’t you?
So how do they get around a required code? They just ask you for permission, of course.
Let me share a scenario with you. You get into work one morning and sit down at your computer to check your emails. You see an email from a co-worker saying they are sharing a report with you.
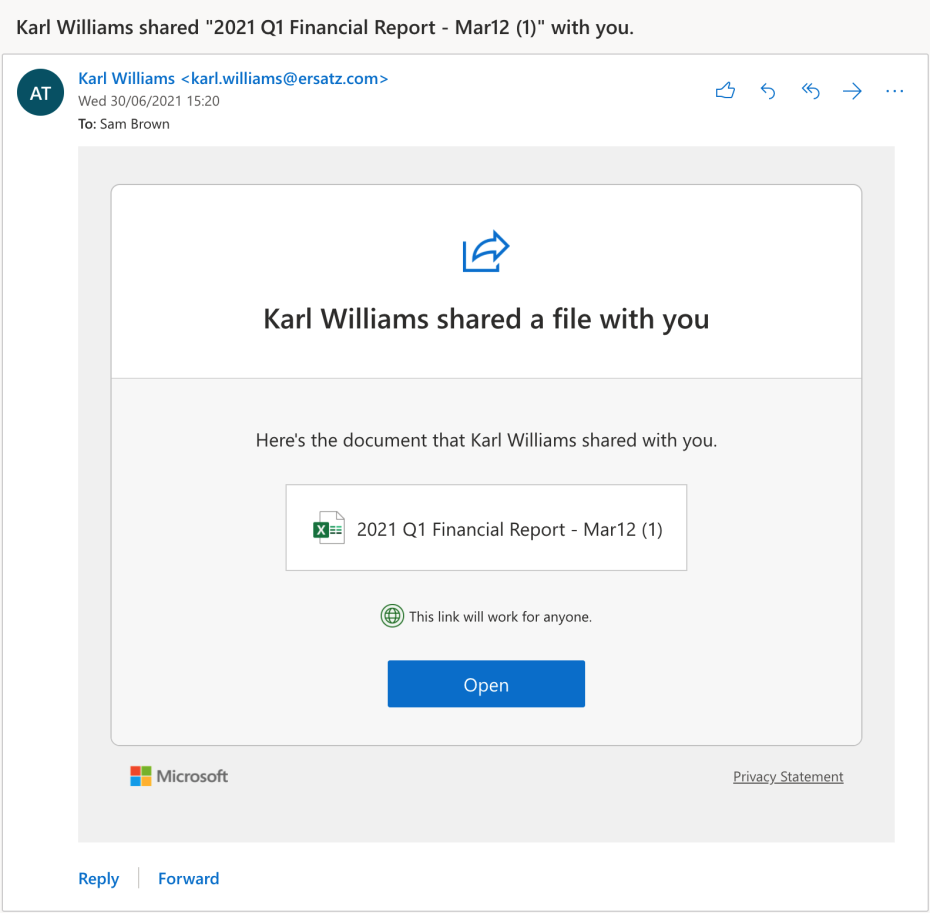
You think it’s a bit weird that Karl would send this report to you, but you click through to open it because maybe the file has some information you need. And up pops a permissions request similar to one you’ve seen before.
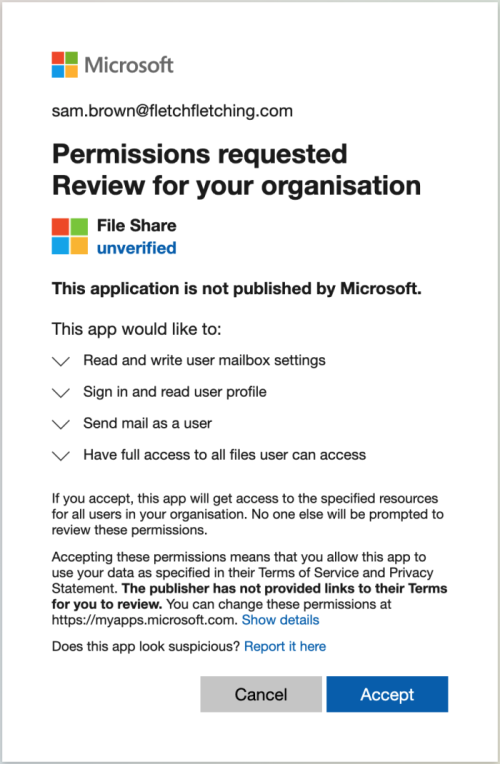
Okay class. Who can tell us what should be activating your spidey senses right about now?

Here are things that should set off red flags and alarms in your head:
- Even though there is a Microsoft logo at the top, you can see that it clearly says that this application is not published by Microsoft. They really try to make it look legit, even offering an option to report it as suspicious…but it doesn’t make it legit.
- Organization is misspelled. Multiple times. For as smart as the bad guys are, they usually aren’t great spellers.
- Look at the permissions that the application is asking for – read and write in your mailbox settings (where someone could change your password, change your forwarding, etc). They can sign in as you, send mail as you, and access ALL of your files that you have access to.
- They also are very clear that they are not providing links to their terms for you to review. That’s really because they don’t have any terms! Tricksters.

Now the hope is that you remember this tip, you see the red flags, and you don’t click through to the file. However, if I don’t finish the story my tip is kind of incomplete.

If you click through to the file, guess what? Not only will you realize that Karl didn’t need to send you that file, you’ve just given the bad guys permission to access your account. Anytime. And without 2 factor authorization. And just like that, a security feature that should protect your email and files is no good anymore.
So a reminder to always be mindful of the things you are clicking on, always pay attention to what permissions things and people are requesting, and NEVER ignore your tingling spidey senses.