Impersonators aren’t a new thing, right? They’ve been around since…..well…..at least since Elvis. So...
Blog
Tips, Tricks and News from your trusted IT partner.
Well. Life is upside down. I feel like we’re all playing a huge game of Don’t Touch the Lava. You kn...

As many of us have adjusted to working from home for a month or more now, what are you finding that ...
So, you’ve decided that your business needs a server and now you’re wondering why you can’t run it o...
I consulted with a small business last week. Their server had stopped powering on a few weeks ago. T...
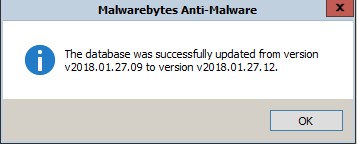
It has been widely reported this morning that MalwareBytes was causing an issue blocking legitimate ...
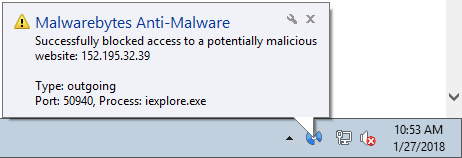
If you’re having a problem this morning accessing your email or other network resources or websites,...
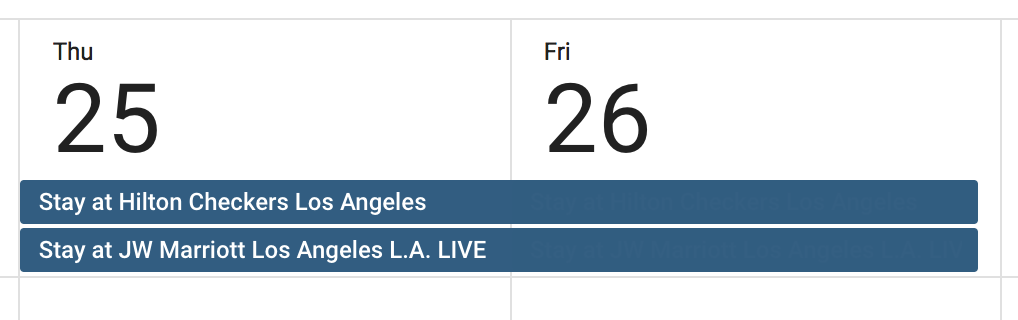
If you’ve recently booked a hotel, a flight or some other things like restaurant reservations or con...
Guys. Let’s get serious for a second.

Are you getting mail through a group address? For example, you might be a member of a support or acc...
Subscribe to Updates
Southern California's Premier Technology Success Provider
Get in touch today to see how we can keep your business In Motion!
